NTP Reflection attacks which began at the end of 2013 have reached 400 Gbps that the highest size of attack has been detected in the world in 2014. After DNS attacks recorded as 300 Gbps in March 2013 and targeting spamhaus, attacks have seen as 400Gbps of traffic size in 2014.
These attacks can reach these high levels by using mirror method. As happened in DNS Reflection flood attack type, mediator innocent public server systems are used as a point of attack in this type of attack.
The attacker is querying NTP servers in an intensive way but gives the IP address of the target system by changing its IP address deliberately while querying. This is because of that the NTP protocol running over port 123 is based on UDP. In this case, NTP servers are responding the queries made to them, but the answer of this query is returning to the target system appears as IP address asking the query. As seen in this type of attack, public NTP servers are used as a mirror.
The key factor in achieving this size of attacks is query type known as “monlist” in NTP protocol. In this query type, NTP server lists the last 600 server connected to it or set in pieces.
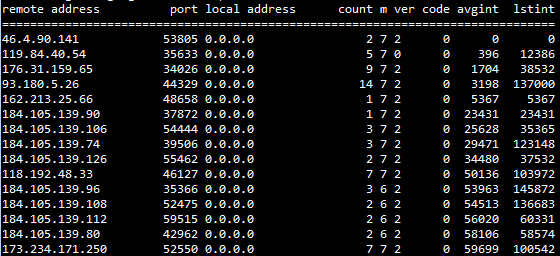
Getting an answer to a query containing a large number of IP is possible by making monlist query with a very small package size. At this point, NTP server is making an “upgrade”. “Amplification” as the English term is taken place. Thus, this type of attack is called as NTP Reflection and is also called as NTP Amplification attacks. Of course, the answering the question with larger packages than query is a golden blessing for attackers. In this way, the attacker takes enough answer to the queries to target IP address by imitating the IP address wanted to attack.
The following points should be noted to protect from this attack or not to be a part of it.
1. If you operate an NTP server, you should do your updates in which the versions of this command are turned off. In addition, as well as “loopinfo” and “iostats”, you should turn off NTP server configuration to “monlist” commands. For the test, you can use the control screen on “http://openntpproject.org/”.
2. You should follow monlist connections to public NTP servers out of your network. You can do this by means of an IPS signature. This may show you a possible zombie on your network.
3. You should try to prevent L3 packet speed with firewall of response packets coming from NTP server or “monlist” answers by checking content with the IPS via your security gateway.
We want to indicate that all of these can be made by Harpp DDOS Mitigator that performs DDOS special examination in L7 level. Thanks to Harrp DDoS product, various measures can be taken against related attacks in systems under L7 specific protection. Protocol Review and Defining Private Rules come at the beginning of these measures. You can determine the number of packages and regions you can get at certain times and in certain proportions in your Special Rules for NTP queries or answers or you can directly prevent this specific queries and answers with L7 review.
3
MAR
Share


